From viral marketing to computer viruses, the cultural logic of virality permeates the Web. The December 2010 issue of the Sage journal Body & Society will publish my long-awaited 36-page essay “A History of Virulence: The Body and Computer Culture in the 1980s”. The text that follows is the first part of the “author’s cut” version of the article: an archeology of computer-mediated moral panic, autonomist marxist hacking, and AIDS activism. Click here for the second part.
Ubiquity, Embodiment, Virality
The emergence of ubiquitous media and the focus on pervasive computer networks seem to have introduced a major shift in the way information and communication technologies are practised and represented in contemporary societies. Since the early 2000s, the consensus around theories of a virtual humanity ‘homesteading on the electronic frontier’ – the ethereal cyberspace where users were to be ‘uploaded’ (Lévy, 1994; Rheingold, 1993) – have progressively given way to approaches to computer-mediated social interaction centred on mixed realities. According to these new theoretical stances, digital technologies are to be regarded as a domain of affordances extending and enhancing physical presence rather than superseding it (Hansen, 2006). Significantly enough, the author who popularized the very notion of ‘cyberspace’, William Gibson, acknowledges this momentous development in his novel Spook Country: if the pre-ubiquitous technological paradigm can be described as ‘a state in which ‘‘mass’’ media existed, if you will, within the world’, in the ubiquitous one they ‘comprise it’ (2007: 121).
Ubiquitous computing does not transcend everyday experience, rather it pervades reality by saturating the actual space of the cities and by infusing physical bodies. Featherstone (2007: 320) describes this media ontology by suggesting that ‘as media become ubiquitous they become increasingly embedded in material objects and environments, bodies and clothing, zones of transmission and reception’. After Simondon, Bernard Stiegler defines social and ubiquitous media as a ‘human techno-geographical milieu’ (in Venn et al., 2007), that is, a socio-technological process converting human corporeality into information. Following Stiegler’s emphasis on the need to harmonize symbolic, technical and material milieus, new couplings of the body, social imaginaries and social practices come into view.
As far as all reality can be considered as a mixed reality, the theoretical issue at stake is what the social and cultural mechanisms are for allowing the mutual introjection of information and communication technologies (ICTs) and human life. Knorr Cetina and Preda (2007) aptly remark that the distinctive feature of contemporary communicational systems is their capacity tosubsume and, at the same time, to project the life-world. Digital embodiment, thus intended as one that does not renounce physical presence yet reconfigures it in a dialectical exchange with the technological artefacts, emerges as the central topic of contemporary computer culture. In contrast to the early warnings of the renunciation to the ‘real’ body (Le Breton, 1999; Moravec, 1988; Muri, 2003), more recent trends in science and technology studies point towards the dismissal of the ‘disembodiment’ hypothesis (Casilli, 2009a; Hayles, 2009).
This, nonetheless, leaves open the question as to the historical reasons why the set of theories insisting on technologically induced disembodiment prevailed in the first place. In this article I will maintain that both the disembodied and the ubiquitous discourse surrounding the body and information technologies represent the actualization of a certain cultural feature, namely a rhetoric of virulence, which is not new to computer culture. Contemporary focus on ‘viral’ circulation of online contents on the Internet and its impact on the economic and political spheres (Krishnamurthy, 2004; Painter, 2002) echoes elements of biological and informational danger that have been evident since the early years of mass computing. The biological metaphor also mirrors a social dynamic based on the premise of the information permeating the body. Following in the current trend of research addressing the societal impact of information and communication technologies in a historical perspective (Bell, 2007; Bell et al., 2004; Sterne, 2006; Tofts et al., 2003), the present article aims to examine the emergence of this rhetoric as a historically situated construct resulting from the juxtaposition of two social processes: (1) the reaction of mainstream media and public opinion to burgeoning autonomous computer usage on a potential mass level; (2) the alliance of computer activists and HIV/AIDS right advocates, relying heavily on technological expertise to promote public campaigns challenging biomedical authorities and public health policy-makers.
Methods
Sources
Mainstream press and underground publications dealing with computer use provide an opportunity to examine how notions and beliefs surrounding the body have been expressed, both in written and iconographic form. Html versions of newspaper articles and scanned files of specialized publications from the 1980s were analysed to gain insight into how the discourse of virulence was built, both inside and outside computer culture.
The main sources analysed were of two types: written and iconographic. The first set of sources was extracted from the online LexisNexis Executive service. A body of 654 articles and newswires published between 1 January 1985 and 1 January 1991 in English-speaking international publications was examined.1 The second set of sources was extracted from specialized publications targeting computer users. The analysis was carried out both on the underground press (31 issues of the German-language journal Datenschleuder, dated 1984 to 1991) 2 and on the consumer press both in French and English (31 selected images, dated 1982 to 1990). 3
Data Analysis
A system of category codes was developed through an iterative reading of the articles (first set of sources), and through an examination and comparison of images (second set of sources). The approach involved isolating units of analysis (either written passages or details of images) and identifying threads and visual tropes. The units were then coded according to dominant themes and arranged into two parallel non-hierarchical inventories.
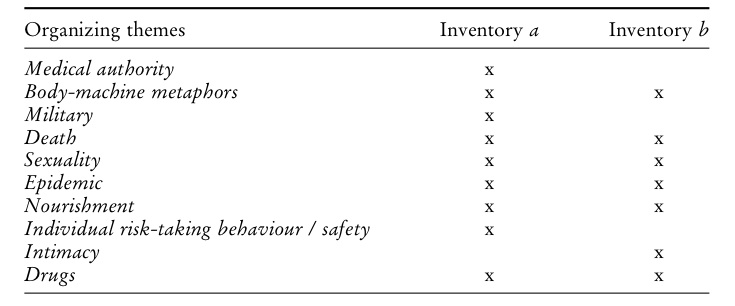
Figure 1 – Organizing themes for the two inventories of sources
Computer Viruses: Inscribing Computer Culture in the Biomedical Domain
At the moment of their introduction, new social practices associated with computational artefacts were perceived as inhabiting a legal and cultural grey area. In the second half of the 1980s, autonomous computing 4 – a loose definition that encompasses semi-legal computing activities such as file downloading, sharing and free-code development – started to be linked with pollution and contagion. As the media attention to the AIDS pandemics reached its peak, the mainstream press began adapting metaphors of virulence and ‘unsafe behaviours’ to autonomous computing, thereby creating one of the most interesting features of late 20th-century technological discourse: the notion of computer virus. Initially popularized within the software engineering community around 1984, this expression designated a malicious code with the ability to modify other computer programs and turn them into ‘infectious malware’. In this section of the article, I will examine how the discourse of computer contagion came into common use and became the central element of a moral panic campaign in subsequent years. 5
The analysis of mainstream press sources provides an overview of the shifts of metaphoric and semantic associations played out in newspaper stories. The turning point of this development can be situated in the year 1988. Before that date, the metaphors that were most commonly associated with malevolent computer use were of military origin. Hackers would ‘attack’ and ‘invade’ operating systems in order to ‘spy’ on them, or even install ‘logic bombs’. Malicious software codes would exploit system ‘vulnerabilities’ and cause ‘breaches in security’. Around 1988, this military terminology is progressively abandoned in favour of other metaphoric turns.
In the corporate world, for instance, management of the ‘health of the information technology environment’ starts to be coupled with the management of the health of the employees. The tip-off is provided by a short Associated Press newswire. The title itself explicitly endorses the imaginary superposition of bodily pathology and computer malfunction:
COMPUTER VIRUSES ARE HIGH-TECH COUNTERPARTS OF BIOLOGICAL VIRUSES – Just as a biological virus disrupts living cells to cause disease, a computer virus is a parasitic computer program that invades data processors and reproduces itself to disrupt normal operation of the machines. Biological viruses are pieces of the hereditary code that take over a living cell’s machinery to trick it into making thousands of duplicates of the original virus, infecting more cells to cause disease such as AIDS, which cripples the cells that defend the body against infection. (Associated Press, 1988)
The parallel between the body and computers is thus established. The keywords are all in place: ‘virus’, ‘AIDS’, ‘infection’. To see how they play out in this body of literature, it is useful to look at a second theme, that of medical authority. Computer security experts are indeed compared to medical practitioners. Management is exhorted to use security professionals ‘just as they would use a medical professional when serious illness threatens’ (Wilder, 1988). From this point on, metaphors are mostly drawn from a discursive repertoire that revolves around the idea of virulence. Described as ‘illnesses’ jeopardizing informational ‘health’, viruses allegedly create a need for the ‘doctoring’ of electronic artefacts. The trade names developed for the first commercial anti-virus ‘medicines’ are unequivocal: Data Physician, AntiDote, Flushot, Panacea (Rosenberg, 1988). There is no cause for surprise that the threat embedded in computer use is described as a hazard for the user’s bodily integrity. As governments allegedly recognize their powerlessness to fight hackers via warfare or law enforcement tools, the only way a computer epidemic could be policed – journalists maintained – is by assigning to each and every citizen the mandatory management of risk-taking behaviours. In the press, reports of the damage produced by computer viruses become cautionary tales, comparable to the moralizing discourses on hygiene in the early 20th century. Far from being simple metaphors, these warnings against the propagation of infections urge a new ‘civilizing process’ that addresses both corporeal and digital behaviours.6
HIV/AIDS, as the distinctive disease of the 1980s, came to play a major role in the computer virus imaginary. Reaching further into the intimate sphere, technological contamination is purported to be able to take the form of a sexually transmittable disease. While commenting on the arrest ofRobert T. Morris – a young software engineer accused of having launched the first self-replicating ‘worm’ (at the time an exotic type of computer virus) on the Internet (at the time, an almost unheard of computer network) – security experts let slip that ‘with Robert in hand, safe computing, like safe sex, is attainable’ (Associated Press, 1988). The effort to exploit widespread sexual anxieties encouraged industry actors to push even further the inscription of autonomous computing practices into the linguistic domain of biomedicine. Hospitals, pharmaceutical companies, scientific research centres, became the new elective targets of ‘computer criminals’.
Hacking thereby increasingly becomes a problem of public health. The pharmacoms are first in the firing line. A Financial Times article rather blatantly compares computer pirates attacking the electronic system of a condom producer to the Chicago extortionist who was responsible for the infamous 1982 Tylenol case (Abrahams, 1988: 17). Apart from the reference to sexually transmissible diseases (implied by the very nature of the business targeted), computer intrusions are held responsible for obstructing private companies in their search for a solution to AIDS and for forcing them out of business (Abrahams, 1988: 17). Hospitals were soon added to the long list of victims of computer misdemeanours. Although, as a matter of fact, clinical establishments were reported having suffered hacker intrusion even prior to 1988,7 in the wake of the computer virus moral panic, ‘computer criminals’ are customarily accused of interrupting therapies, damaging clinical equipment, and threatening the safety of doctors and patients.
Moreover, media commentators agree that medical files are easy prey for hackers. In a 1985 Australian press agency report, the theft of sensitive data is depicted as an actual danger for all Queensland users, who – it is claimed – would be defenseless against blackmail by computer-savvy youths (Rodgers, 1985). In 1988, the authorities of the Australian state of Victoria are accused of not having adequately protected the personal data of the donors to a sperm bank. This alleged incompetence exposes the donors to the unpleasant possibility that the babies that had been born might ‘come knocking at their door’ because of possible breaches of the electronic databases containing their name and address (Peak, 1988).
As if the shadow of blackmail was not enough of an intolerable blow to individual privacy and safety, other, far more tangible, catastrophes are conjured up in the event of computer delinquents targeting healthcare services. Malicious software could potentially infect data relative to important research projects, a scientist from the UCSF declares to a Christian Science Monitor reporter (Bradley, 1988). But, a few lines on, he contradicts himself: not only does the hospital keep a printed back-up of these data files but their research computers aren’t even online. All the same, computer experts and media agree in saying that ‘a virus in a hospital computer would create a chaotic, perhaps life-threatening, situation’ (Bradley, 1988: 3). Although the actual danger to the medical establishment is extremely limited, autonomous computer activities could pose threats to patients for the simple reason that they throw the therapeutic process into confusion. Clinicians are ideally depicted as dealing with severe illnesses and life-or-death situations. The slightest interference is therefore presented as having potentially fatal consequences. The main concern expressed by the medical community is that hackers’ displays of technological proficiency distract them from their main task – ‘saving lives’ (Harrison, 1988).
When real events do not quench newspapers’ thirst for computer virus stories, many outrageous hypotheses passed on by self-appointed experts are used instead. Press features turn into pulp fiction, providing lurid details and vague information when it comes to places, dates, persons concerned. Ironically, this vagueness has the unexpected consequence of universalizing such stories by reinforcing their exemplary character:
In one incident, an unidentified hacker gained access to the computerized patient records of a Los Angeles hospital and changed all intensive-care patients’ entries to double the prescribed drug dosages. Fortunately, hospital officials discovered the penetration before the altered records caused potentially fatal drug overdoses. (Wood, 1988: 28, emphasis added)
The similarity between computer viruses and AIDS invites management of the risk not only at the individual level. Once an association is established between data safety and potential death threats, the epidemiological implications come to be seen as threatening to society as a whole. The anxiety surrounding the connection between computers comes to mirror the bundle of fears that surround bodily contact. Whether organic or electronic, these two types of communication both become inscribed in a biomedical frame of virulence. After 1988, the general public started perceiving HIV/AIDS not as a problem confined to certain minorities (homosexuals, Haitian immigrants, intravenous drugs users, etc.). HIV/AIDS could strike ‘anybody anytime’. Sexual exclusivity, prophylaxis, security measures aimed at preventing the spreading of the epidemic were not in themselves sufficient any more. A similar evolution is detectable in the discursive structures of the debates about computer misuse.
This point is made all the more vivid in one of the most striking media stories of the late 1980s: the AIDS diskette saga. On 7 December 1989, 26,000 computer diskettes containing an ‘interactive program for health education on the disease called AIDS’ were sent throughout Europe and Africa from an obscure London-based company. While users were to answer an electronic questionnaire that assessed risk-taking behaviours and suggested strategies for coping, the diskette installed another piece of software – a trojan horse that would lock the hard disk and display a message asking payment for an annual license subscription of US $189. Evidence collected by Scotland Yard was inconclusive. Some of the addressees included participants of the previous year’s World Health Organization (WHO) Stockholm AIDS international conference. The rest were subscribers to the magazine PC Business World. The producer of the software turned out to be a shady organization called PC Cyborg Corporation, based in Panama. However, the country was virtually inaccessible at the time because of the US military operation to overthrow General Noriega’s regime. An unexpected set of coincidences (the finding of a PC Cyborg rubber stamp during a routine baggage inspection at Amsterdam Schiphol Airport) eventually led to the arrest of an American citizen: Harvard-trained anthropologist Joseph Popp. Popp himself was an associate of the Flying Doctors, a branch of the African Medical Research Foundation (AMREF), and a consultant for the WHO in Kenya, where he had organized a conference in the new Global AIDS Program that very year.8 The media pounce on the news scoop, which perfectly fits into the previous discursive thread. The story has all the right ingredients: an electronic threat, a police mystery and a terrifying disease. The AIDS diskette case is initially presented as yet another assault on medical institutions by a subversive computer criminal. The damage caused to hospitals and other health establishments by the trojan horse is exaggerated. The financial loss, initially estimated at the stratospheric amount of £6 million, pales by comparison with the alleged public health threat represented by the malicious diskette. The Guardian announces that ‘several’ diskettes have been sent to medical research laboratories (Large, 1989). The Australian Advertiser, maintains that a London charity dealing with AIDS prevention has received ‘several hundred copies’ of the software (Murche, 1989). The Washington Times, for its part, reports that an ‘uncertain number’ of European hospitals have been hit by the virus (Richman, 1989), and that catastrophe was avoided in the US thanks to the prompt mobilization of AIDS researchers.9
After the main suspect is arrested, the press persists in playing up the threat to public health by emphasizing the anthropologist’s doctoral title. ‘Dr Popp’ comes to be portrayed in the media not as a computer extortionist, but as a maverick scientist engaged in a lone project of medical prevention and information dissemination. Emphasis is put on his links to HIV/AIDS research, the WHO and African medical associations. According to The Guardian, Popp was on a mission for WHO to study AIDS in Africa only a few months before his arrest (Brasier, 1990).
The AIDS diskette is unlike previous computer hacking stories. All the tropes of computer virulence are portrayed, but in a more complex and ambiguous way. The hacker is assuredly designated as the carrier of the malicious code. But, paradoxically, his computer virus is designed to fight a real-life one. Dr Popp is presented as a heterodox practitioner aiming to heal through computing. An Associated Press newswire of February 2nd 1990 describes him as a ‘medical-informatic consultant’ (Associated Press, 1990a). Not a clinician, but a healer working in AIDS education, or rather a ‘specialist . . . developing informational programs’ promoting a new kind of information-driven treatment (Pane, 1990: 43). ‘The Doctor’ is no ordinary hacker, just a non-conformist health specialist, and a rebel against the medical establishment. He is led to hatch his diabolical plot because of his ‘frustration with the pharmacom-ridden medical research on human immunodeficiency’ (Connor, 1991). Between the lines, it becomes clear that Popp’s autonomous computing activity is intended to promote an alternative model of medical research. In his press statements, the anthropologist himself poses as an adversary to his former employer, the WHO, and official health policies. His scheme is, in his words, aimed at raising funds for alternative research and for non-profit HIV/AIDS organizations. ‘The sole reason for the project’, he insists, ‘was to use computers to provide health education to people around the world to fight the global epidemic of AIDS’ (Associated Press, 1990b).
Over a two-year period, the dramatic tension around ‘deadly viruses’ polluting computers reaches new heights in the mainstream media. A simple metaphoric juxtaposition between bodily and technological contamination, triggers a complex narrative weaving together of intimate fears and public health risks, physical and informational dangers, threats to the body and threats to communication technologies. The AIDS diskette story represents an unexpected turn in the virulence discourse. This dystopian parable turns out to contain a utopian promise: the spreading of a computer virus comes to represent the possible end of a physical disease. This paradox, as I will explain in the next section, is also one of the main features of the discursive construction of virulence in the specialized and underground computer press.
- The texts analysed stem from the archives of the online service LexisNexis Executive. Research was conducted under the category ‘major international publications’ in English. Keywords: +hacker. +computer crime, +hacking. ↩
- The online archives of the hacker fanzine Datenschleuder available on the website ds.ccc.de, were last accessed through the servers of the Ecole des Hautes Etudes en Sciences Sociales (France). ↩
- The images, located in a database accessible on the website www.old-computers.org, were consulted through the servers of the Ecole des Hautes Etudes en Sciences Sociales (France) ↩
- In this article, I prefer the expression ‘autonomous computing’ over ‘free computing’ to describe the participatory and non-institutional usage of information and communication technologies. The notion is loosely inspired by that of ‘autonomous technology’ introduced by Dyer-Witheford (1994) and Di Corinto and Tozzi (2002). As such, it is closer to the political context of the early 1980s and less prone to anachronism than the notions of ‘free’ or ‘open’ computing (Raymond, 1998) ↩
- Although their existence was attested in the 1970s, it was only in the following decade that electronic viruses started to be perceived as an actual danger by the software engineering community. The first scientific article analysing and defining them is Cohen (1984). ↩
- This assumption is developed in Kocher (1989). ↩
- In a memorable case dating back to August 1983, the radiotherapy department of New York’s Sloan-Kettering Cancer Center was infiltrated by the members of the ‘414 gang’, a hacker collective from Milwaukee. Probably performed by mistake and promptly interrupted, the access was depicted in sinister tones in media reports. In this case, the system administrators at the Sloan-Kettering Cancer Center solved the problem by simply sending the hackers a message asking them to stop their jokes – which they did immediately. There was no damage to the system. ↩
- For a complete reconstruction see Mungo and Glough (1992). ↩
- No American addresses were targeted and the diskette’s licence agreement formally banned distribution and use of the software in the US. See Anon. (Popp, Joseph L.?) (1989). ↩