From viral marketing to computer viruses, the cultural logic of virality permeates the Web. The December 2010 issue of the Sage journal Body & Society will publish my long-awaited 36-page essay “A History of Virulence: The Body and Computer Culture in the 1980s”. The text that follows is the second part of the “author’s cut” version of the article: an archeology of computer-mediated moral panic, autonomist marxist hacking, and AIDS activism. Click here for the first part.
Computers – Viral or Visceral?
This ‘viral turn’ in mainstream computer narratives was absorbed in a somewhat paradoxical way into users’ milieus. The symbolic coincidence of the body and computing machinery, as well as the related viral motives, were enthusiastically adopted by computer amateurs. This appropriation can be read as a typical ironic strategy mirroring hegemonic taxonomies (Ang, 1985; Storey, 2006), a way of transcending labelling through self-stigmatization. In this sense, virulence developed into a cultural process of unapologetic ‘counterpride display’ typical of youth subcultures (Richards, 1988). In the context of 1980s computer culture, this can be interpreted as something that aimed not only to empower autonomous social practices through political recognition but also to normalize personal motivations and behaviours through the inscription of technological activity in the intimate sphere of the body. The mimicking of the media hype was not only performed with satirical intent. It also performed a deliberate distortion and amplification of the viral discourse into one of ‘viscerality’. The classical Cartesian superposition between body and machine – implied by the mainstream rhetoric of computer viruses – expanded into a thematic sequence that came to be dominated by the image of the machine penetrating the body.
Understanding how computer culture adopted the stigma of being a ‘virus’ and turning it into an asset requires first understanding the relative place and status of the computer in late 20th-century consumer culture. The process of miniaturization of computing technology that had led from the 13-ton UNIVAC (1951) to the 30-odd kilo IBM 5100 (1975), was also a process of re-territorialization. While the post-war ‘electronic giant brains’ (Berkeley, 1949) occupied military bunkers and industrial basements, the 1980s saw the infiltration of computing machines into the private sphere. Decades before ubiquitous computing, homeand family-computers took up residence inside the houses of a new generation of electronic amateurs1. Commercial names changed in step, evoking everyday life and homely informality. The most successful products had common male and female names like Lisa or Vic2. They conjured up the unthreatening pleasures of family life: children (Junior, Piccolo), small animals (Pet, Bee), and fruits (Apple, Acorn, etc)3. Products designating power, luxury and imposing size were destined to sell poorly4. Specialized press targeting computer users developed these motifs. Home privacy became synonymous with personal, bodily intimacy. In the media, there was an increasing trend to emphasize the association between autonomous computing and bodily performance, beauty and health. The well-known Apple 1984 TV commercial (Scott, 1984)5, for example, staged the liberating power of personal computers by opposing a young female athlete to a crowd of senile users living under the rule of an Orwellian Big Brother.
These initial remarks are corroborated and extended by the analysis of visual sources. At first glance, the depictions of computers associated with sports and physical activities duplicate this buoyant bodily imaginary. For example, Figure 2 clearly places the computer in a family setting. The presence of a father and his son suggests intergenerational unity and family ordinariness. The father wearing sports gear further indicates that computing can be seen as a substitute for physical exercise.

Figure 2. Family computer and physical exercise (Anon., 1983a – courtesy of old-computers.com)
Figure 3 similarly stages the complementarity of physical exercise and computing: a woman sitting on the floor of her living room is performing an aerobic routine, following the gestures and positions displayed on the computer screen placed in front of her. The copy reads: ‘Enter your heart rate and your age, and it will put you back into shape.’

Figure 3. Personal computer enables physical performance (Anon., 1983b – courtesy of old-computers.com)
In this context, the emphasis placed on the private dimension of the technological experience exorcizes the perils associated with public spaces: computers are ‘safe as houses’. Yet, underneath this positive imaginary, something else takes shape. Computers are getting closer to the body, touching it. A hand strokes the mouse, a face approaches the screen, a chest leans over the keyboard. New, ‘portable’ micro-computers virtually begin to stick to the body, to the trunk, to press against the entrails. In Figure 4, the French computer journalist Alain Tailliar strikes a pose in an old promotional press photo that is precisely a testimony of the surfacing of a new visceral approach to computer usage.

Figure 4. The computer ‘sticks to the body’ (Anon., 1982 – courtesy of old-computers.com)
Although the size of the computer in the image might bring a smile to the face of present-day readers, at the time it clearly aimed to present an over-optimistic, idealized vision of information technology. But the handsome, open-hearted Cary Grant-type character also betrays an inner tension, which is exemplified by his squinting eyes and his clutched hands. The rigid gesture of his two arms is the central element here, as they round off in a circle, to bring the computer close to the stomach and squeeze it against the torso to interiorize, to embody it.
Eminent voices in the computer underground, who were actually never far from commercial culture, echo this fascination. Bruce Sterling describes the new information technologies as ‘pervasive, utterly intimate’. Personal computers are no longer external to their users, but next to them: ‘Eighties tech sticks to the skin’ (Sterling, 1986: 12) and sometimes it even goes so far as to penetrate under the skin and into the body. The 1986 ‘Hacker Manifesto’ (The Mentor, 1986) effectively completes the metaphor by comparing computer hacking to intravenous drug use6 We exist without skin color, without nationality, without religious bias … and you call us criminals. [ . . . ] My crime is that of judging people by what they say and think, not what they look like. (The Mentor, 1986).]. References to HIV/AIDS and risk-taking behaviours are not alien to the computer iconography of these years, but, in comparison with the written resources examined in the previous section (‘Computer Viruses: Inscribing Computer Culture in the Biomedical Domain’), they are more tangibly connected to images of internal circulation, secretion and subcutaneous pulsation. Viscerality hooks up with virality in conveying a bodily imaginary which relied heavily on deep organs, entrails and fluids. This discourse is best highlighted in the iconography of the German hacker fanzine Die Datenschleuder7 was initially published as a xeroxed newsletter by the Chaos Computer Club (CCC). This historical collective of anarchist and autonomen computer activists first made international news in 1984, when the German computer network Bildschirmtext was hacked. CCC members managed to withdraw a large sum of money from a Hamburg bank. Along with typical hacker bravado, the CCC founders displayed a certain ‘gentlemen Marxist thieves’ integrity: the money was soon returned and the act remained simply a bold commentary on the financial system’s greed.]. The theme of sexuality recurs throughout the first issues, used as a means to alternate technical articles, political commentaries, spoof and satirical illustrations. The cover of issue no. 19 (Figure 5), features a scene of seduction. In a richly furnished bedroom, a libertine kisses and fondles a sensuous lady revealing her generous cleavage. While the lovers touch each other, their hands wander over the keyboard of an elegant 18th-century decorated computer.

Figure 5. Sexualizing the computer: parody of computer ‘intimacy’ in a 1980s hacker fanzine (Anon., 1987 – courtesy of ds.ccc.de)
The inclusion of electronic artefacts in the intimate sphere of their users is here overplayed to the extreme. The family is condensed into the couple, the living room becomes a bedroom, and innocent playfulness is misrepresented as foreplay. If in the specialized commercial computer press, the technological artefact commanded a libidinal investment from its consumer, here it releases the unashamed display of a libidinous behaviour.
Also, in the case of Die Datenschleuder the logical gap separating the intimate/private sphere from the corporeal one is bridged. The hacker fanzine starts playing with the motif of the bodily assimilation of computers, going so far as to suggest that computers are edible, ready to be absorbed and literally incorporated by their users. A collection of mock ‘Gastrocybernetic’ computer cooking recipes proposed in issue no. 17 (Anon., 1986a: 13), paves the way for a restricted but significant set of images published around 1988, representing users actually eating computer terminals (Figure 6).

Figure 6. Hunger for information: incorporating the computer through ingestion (Anon., 1988 – courtesy of ds.ccc.de)
The desire for computing that in Figure 5 took the form of sexual urge, here becomes hunger for information. Not only it is suggested that computers are an object of appetite, but also that the final locus of information is the inner recesses of the body itself.
In the hacker imagery, people are presented as eating, fondling and making love to technological artefacts. The close relationship between technology and the human body would soon foreshadow notions of contamination, pain and agony. However, prior to 1988 it is the elements of fun and play that tend to predominate in the description of the symbiotic fusion between humans and computers. If virality is evoked, then it is done through representations that depict the virus floating over, or ‘riding’ the body and its organs such as, for example in Figure 7.
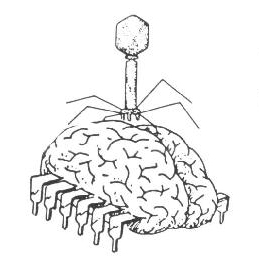
Figure 7. The virus ‘riding’ the organs of the body (Anon., 1986b – courtesy of ds.ccc.de)
Humour and sexual innuendos are still quite present in this image, but they are also mingled with a diffuse sense of dread and danger, exemplifying what Van Loon (2002) dubs as ‘the jouissance of viral terrorism’. The human anatomy and the virus are presented as sharing the same nature (they are both ‘bugs’, which is what seems to be suggested by the brain’s cockroach legs). Even so, they remain two distinct objects, and do not permeate each other.
For permeation to occur, the dense and solid qualities of the organs need to be liquefied. Playing on a macabre repertoire, German hackers start exposing physical decadence and necrosis. On the same synchronic axis used to analyse the mainstream press sources in the previous section (‘Computer Viruses: Inscribing Computer Culture in the Biomedical Domain’), the motifs of computer virality and viscerality become detectable after 1988.
The user’s body comes to be represented as a corpse ‘secreting’ information as a blister would secrete pus. On the cover of issue no. 30 (Figure 8), an animated skull mocks the German postal authorities warning: ‘This communication might have been opened for inspection’. To add morbidity to the image, from the zipper-lined open wound on the top of the skull, a slimy substance spurts out.

Figure 8. Informational virus as liquid infection (Dizzy, 1989 – courtesy of ds.ccc.de)
The sinister jubilation that underlies this type of image could be interpreted as a provocation, a satirical exaggeration of the media discourse. What in the mainstream newspapers is mere insinuation was openly and loudly proclaimed in the hacker fanzine.
This contamination clearly works to evoke images of fluidity and liquidity. The virus inside the skull turns the brain into seepage. Information becomes a disease circulating in the body, which is obviously evocative of the liquid elements of the AIDS/HIV narratives – semen, blood, etc.
How to Have a Body in an Epidemic
The parallel unfolding of motifs of virulence in two different media contexts shapes a discursive repertoire that interconnects computer safety to public health issues, and technological artefacts to the body. Explaining that requires a better understanding of the strong discursive link between computer virulence and the AIDS moral panic, which can be achieved by taking into account the sociological and cultural circumstances surrounding computer culture in the 1980s. The HIV/AIDS pandemic was actually the sign of a deeper crisis in the controlling and protective function that the biomedical establishment (clinical professionals, scientific research experts, pharmaceutical companies, public health agencies, etc.) had exerted over the body throughout the 20th century. As clearly pointed out by Cooper (2006), the 1980s was a time of ‘epidemiological transition’: on the one side WHO and the UN announced the defeat of infectious diseases; on the other, major epidemics made a spectacular come-back. While welfare-reduction policies were cutting down public health expenditure, a wide array of new pathogens, infectious and autoimmune diseases would emerge, in both developed and developing countries. The gap between the initial optimism of public health experts and the reality of the dramatic resurgence of infectious diseases may account for the obsessive presence of viral motives within the social imaginary. The sublimation of the viral threat in computer culture may be interpreted, at first glance, as a paradoxical reaction to the failure of medical research.
A wide-ranging social movement took shape around HIV/ AIDS patients, challenging institutional medicine on an international level. The massive use of information technologies, mediated through the presence of a strong core of computer-savvy activists and members of electronic bulletin boards (Gillett, 2003), is a verified feature of this movement. Activist users indeed started setting up networks of HIV/AIDS patients, families, self-help groups and alternative practitioners immediately after the advent of micro-computers. Telecommunications and informatics were at the very core of these ‘electronic civil disobedience networks’8 promoting computer-assisted therapeutic alternatives, conjoining claims and political actions that until then had been dispersed. Some of the most influential pioneers of online communities launched groundbreaking initiatives, such as San Francisco’s Aids Treatment News bulletin or the electronic resource centre Critical Path9. Between 1985 and 1990, several BBS and online databases were made available to HIV/AIDS patients and to their families and friends. Electronic forums such as AIDSInfo, Newsbase Computer or the Gay and Lesbian Electronic Access Network shared articles and up-to-date advice concerning new treatments and prevention. Via computer networks, users throughout the world even managed to attend remotely the Stockholm WHO Congress of 1988 (James, 1988a). In the wake of Cleveland’s Saint Silicon experiment – a telemedicine service that put patients in direct contact with physicians – new modem-based medical advice services were launched throughout Europe and Japan (Grundner and Garrett, 1986; Ikegami, 1997).
As highlighted by Linda Singer (1993) the HIV/AIDS epidemic resulted in an authoritarian discourse in light of which bodies were mobilized, resources were dispensed, and tactics of surveillance and regulation were justified. In order to counter this political and cultural orientation, computer clubs and hacker collectives helped the creation of underground buyers’ clubs and clandestine associations of HIV/AIDS patients purchasing drugs on foreign markets and advocating alternative therapeutic frameworks. Their contribution is also attested in the disclosure of medical information protected by intellectual property laws (Casilli, 2009b). On the occasion of the ‘FDA clinical trials controversy’, autonomous computer users turned out to be crucial for sharing information and coordinating political efforts among militant groups opposed to the US medical authorities (mainly the Food and Drugs Administration and the Surgeon General). This key event revolved around the efforts deployed by US activists to oppose the rigid and time-wasting FDA drug-testing protocols which, according to HIV/AIDS rights advocates, constituted an obstacle to the discovery of effective treatments. All new treatments were routinely submitted first to in vitro analyses (studies of the biochemical characteristics of the drug and animal trials), and then tested in vivo on human subjects. The standard double-blind clinical trial protocol entailed the creation of control groups, the members of which were given simple placebos instead of new (and presumably effective) drugs. From the point of view of the HIV/AIDS community, this standard biomedical method resulted in placebo subjects actually being denied access to potentially successful treatments. Moreover, this process in most cases would take up to seven years from the moment the new treatment was submitted to the FDA, to the moment it was approved for market sale. Facing a scenario of global pandemic, this delay appeared disproportionate for people living with AIDS. In 1987, a massive campaign aiming at a relaxation of the protocols was initiated. The campaign, which would ultimately lead to the deregulation of clinical trials on new HIV/AIDS treatments in the US, represented a momentous event in the history of computer culture and AIDS activism alike, combining their efforts to ‘put drugs into bodies’ while minimizing medical mediation (Treichler, 1991).
In 1988, San Francisco-based Project Inform, the newborn ACT UP, as well as Aids Treatment News (and several other fellow publications), started developing channels of scientific and technological communication. Electronic forums and independent computer bulletins were especially decisive for the organization and execution of several community-based trials, as well as for the successful dissemination of the results (Epstein, 1995, 1996; James, 1988b). These independent experiences successfully managed to place the rights of HIV/AIDS patients for treatment before the internal logics of biomedical institutions and pharmaceutical companies.
Significantly, these events are situated on the synchronic axis that intersects the outbreak of themes of virulence in the mainstream press (see the section ‘Computer Viruses: Inscribing Computer Culture in the Biomedical Domain’) and of virality/ viscerality in the hacker press (‘Computers – Viral or Visceral’). Despite their distinctive succession of themes, both series of sources seem to point to 1988 as being a turning point in the way that the body was featured in press stories about ICTs. The discursive association between autonomous computer users and HIV/AIDS patients is in fact indicative of the formation of a social and political alliance at a particular historical moment. This might also provide a first clue as to why computer culture (especially the hacker scene) did not try to counter the imaginary and discursive association between autonomous computing and virulence. By means of electronic communication and information-sharing, HIV/AIDS patients were increasingly empowered to take a stand and directly challenge public health decision-makers. Computer culture actually helped in the promotion of non-standard therapeutic procedures as well as of critical thinking about contemporary biomedical research. It turned out to be the key to a nascent political subjectivity – one aiming to question clinical powers and their modalities of hierarchical thinking – in its bid to re-appropriate the body as a site of direct participation in social life. The goal of this particular brand of computer user collectives and early online communities was to disseminate medical expertise and multiply the number of actors who were entitled to have a say in the means of bodily treatment, and thus to overturn the prerogatives of the medical establishment over the body.
But another important element influenced the development of the computer virulence discourse: the political reinforcements these militant activities received from the academic milieus of the 1980s. The HIV/AIDS epidemic became the arena in which an array of scholars with no affiliation to medical institutions, but loosely associated with cultural and media studies, launched an attack on the biomedical vision of the body (Lupton, 1994). In the wake of her Cyborg Manifesto (1985), Donna Haraway had already intervened on the subject of virulence by drawing attention to the elements of symbolic and material discrimination that were hidden in the notion of ‘immune system’ (Haraway, 1989). Capitalism, as a socio-historical construction, she claimed, was built upon the ‘purity of the immune system’, that is, on the institution of a socially acceptable bodily norm that legitimized the exclusion of all non-conformist subjects. As spreaders of biological and electronic plagues, HIV/AIDS patients and computer hackers were ripe to join forces with academia’s progressive elements against the 1980s Moral Majority. In taking a common political stance, a shared discursive orientation materialized. The academic left started ‘pleading for virulence’ as the only way out of the corporeal anxieties of the ‘panic body’ (Kroker and Kroker, 1987). To embrace contamination, to dive into the ecstasy of virulence turned out to be the way to declare that, even in the face of the HIV/AIDS epidemic, corporeality was still possible.
The adoption of the viral metaphor over the military one that – as shown at the beginning of the section on ‘Computer Viruses: Inscribing Computer Culture in the Biomedical Domain’ – was hegemonic in the years prior to 1988, turns out to be inspired by a precise political strategy. The centrality of martial images, it has been suggested (Waldby, 1996), proved to be functional to the setting of a political and epistemological order where efforts needed to be mobilized in the name of a ‘war on AIDS’ – and correspondingly of a ‘war on computer crime’. In both fields, the use of military metaphors was intended to evacuate the potential for political antagonism. Eclipsing the presence of computer and AIDS activists alike, media military metaphors tended to divert public attention from social conflicts to a warfare in which only two proper sides (science versus the virus) were detectable. On the other hand, the hacker strategy of accepting virality as inherent to both computer use and bodily experience was intended to subvert from within the logic of immunity – both for organisms and for data. As argued by Allison Fraiberg (1991), the distinctive trait of techno-organic embodiment was its proclivity to contamination. Abandoning any pretension to immune defence, social actors of the information society came to be reconfigured as a matrix of intercommunicating and intercontaminated AIDS-bodies: ‘[t]he traditional, tenuous limits of the body dissolved into fused networks, into open circuits of interconnectedness’ (1991: 21). The adoption of a rhetoric of virulence would allegedly enable the development of a whole set of polymorphous activities that were designed to subtract the denizens of a technology-intensive society from the ‘traditional sites of authority’ over the body, namely ‘bio-medical research, the Surgeon General, governmental and legal policy decisions’ (1991: 28).
Exchanging blood and bodily fluids came to overlap symbolically with exchanging computer files and hardware components: two mutually reinforcing illustrations of the same phenomenon of transgressing the boundaries imposed by clinical powers on the body.
Conclusions
In the above sections, I have argued that the contemporary ubiquitous media approach to the technological body is rooted in a cultural process that originated with the rise in mass awareness of risks related to both computers and to the body in the mid 1980s. Such pairings of apocalyptic and utopian visions of the body were promoted by computer culture chiefly via the construction of discourses about ‘electronic’ viruses (Van Loon, 2002). The focus on the interplay of cultural, institutional and material factors in the construction of the body as a social fact (Detrez, 2002), contextualizes the bodily imaginary of computer culture within the socio-political tensions surrounding computer virulence and the HIV/AIDS epidemic of the 1980s. A set of chronologically concurrent events – generally linked to mass computing and medical controversies – has consolidated the association between material embodiment and informational virality. The rise of a discourse of electronic contamination takes place within the framework of the social conflicts touching on the body – the way it is perceived, regulated, administered. In this respect, this fear illustrates the incessant questioning to which medical powers have been subject during the second half of the 20th century (Turner, 1987).
Indeed, 1980s computer virulence can also be understood as a prelude to the utopias of virtualization and ‘digital regeneration’ of the body that emerged in the following decade. If contamination is perceived as deep-seated in the human body, then human beings themselves, given their material anatomy, are constantly exposed to infection troubling the sterilized world of biomedical prophylaxis. Consequently, early 1990s ‘virtual realities’ came to be saluted as a timely cultural response to the fear trends of the 1980s (Babiole, 1992) and a solution to the stalemate of modern biomedical visions of corporeality. Besides the dreams of disembodiment propagated by the Californian pioneers of ‘cyberdelia’ (Barlow, 1990) or by the heralds of transhumanism (Ross, 1992), applications of virtual realities to surgery, drug design and medical training were among the first to be contrived by their creators. At the world premiere of the datagloves prototypes at Texpo 1989, the then-CEO of VPL Jaron Lanier escorted his audience on a virtual promenade through a hospital’s wards (Woods, 1989). The link between biomedicine and virtual reality came to be reinforced in the following years: after Lanier’s eviction in 1993, Walter Greenleaf – the CEO of a company developing telemedicine applications – acquired the patents for the VPL systems (Hamilton, 1998). Many successful applications of virtual realities in the fields of medical imagery, biochemistry and rehabilitation have been documented in the early scientific symposia devoted to these topics, such as, for example, ‘Medicine Meets Virtual Reality’ or ‘Virtual Reality and Persons with Disabilities’.
If, at the beginning of the 1990s, virtual reality (VR) technologies were welcomed as an alternative corporeal modality, they were also regarded as bearing the promise of a ‘new world order of medicine’ (Satava, 1994) in which information technologies would be more than simple tools for human creativity, and would return to being an institutional apparatus for public health and prophylaxis (Naj, 1993; Rosenberg, 1994).
Present-day ubiquitous and pervasive media, as well as the 1980s discourse of virulence and the virtual utopias of the 1990s, all actually express, albeit in different forms, the same regime of anxieties and expectations about bodily regeneration by means of information and communication technologies.
References
Abrahams, P. (1988) ‘Corporate Security: High-Tech Hits the Old Guard’, Financial Times 22 November.
Ang, I. (1985) Watching Dallas: Soap Opera and the Melodramatic Imagination. London: Methuen.
Anon. (1982) ‘Homo Communicans’, picture in TeleSoft 1: 3.
Anon. (1983a) ‘TI99/4A: L’Ordinateur Familial’, picture in Tilt 3: 23.
Anon. (1983b) ‘Donnez-lui votre rythme cardiaque et votre age, il vous donnera la forme’, ad in Micro07 3: 6.
Anon. (1986a) ‘Die Bratenschleuder: Gastrokybernetische Appetithappen’, picture in Die Datenschleuder 17: 13.
Anon. (1986b) ‘Viromat Plus’, picture in Die Datenschleuder 15: 17.
Anon. (1987) ‘No Title’, picture in Die Datenschleuder 19: 1.
Anon. (1988) ‘No Title’, picture in Die Datenschleuder 28–9: 2.
Anon. (Popp, J.L.?) (1989) ‘Licence Agreement – AIDS Information Introductory Disk’. Brochure. Panama City: PC Cyborg Corp.
Associated Press (1988) ‘Computer Viruses are High-tech Counterparts of Biological Viruses’, Newswire 3 November.
Associated Press (1990a) ‘Man Held on ‘‘AIDS’’ Disc Charge’, Newswire 2 February.
Associated Press (1990b) ‘Man Accused of Computer Extortion Says He Was Set Up’, Newswire 4 February. Babiole, C. (1992) Les Réalité́s virtuelles, documentary film. Paris: Canal +
Baecque, A. de (1993) Le Corps de l’histoire: metaphores et politique, 1770–1800. Paris: Calmann-Lévy.
Bagnall, B. (2003) ‘Commodore – Vic20’, Old Computers, URL (consulted September 2009): http://www.old-computers.com/museum/computer.asp?c1⁄4252&st1⁄41
Barlow, J.P. (1990) ‘Being in Nothingness: Virtual Reality and the Pioneers of Cyberspace’, Mondo 2000 2: 34–43.
Bell, D.J. (2007) Cyberculture Theorists: Manuel Castells and Donna Haraway. London: Routledge.
Bell, D.J., B. Loader, N. Pleace and D. Schuler (2004) Cyberculture: The Key Concepts. London: Routledge.
Berkeley, E.C. (1949) Giant Brains: Machines that Think. New York: John Ziley and Sons.
Berthelot, J.-M. (1992) ‘Du corps comme ope ́rateur discursif, ou les apories d’une sociologie du corps’, Sociologie et socie ́te ́s 29(1): 11–18.
Bradley, B. (1988) ‘‘‘Non-techies’’ Could Be Hurt by Virus’, Christian Science Monitor 80(118): 22.
Brasier, M. (1990) ‘No Bail in Virus Blackmail Case’, The Guardian 3 February.
Burguière, A. (1999) ‘L’Anthropologie historique et l’Ecole des Annales’, Les Cahiers du Centre de Recherches Historiques 22, URL (consulted September 2009): http://ccrh.revues.org/index2362.html
Burke, P. (1986) ‘Strengths and Weaknesses in the History of Mentalities’, History of European Ideas 7(5): 439–51.
Casilli, A.A. (2009) L’Adieu au corps n’a jamais eu lieu’, Esprit 353: 151–3.
Casilli, A.A. (2009) ‘Le Sté́thoscope et la souris: savoirs me ́dicaux et imaginaires numé́riques du corps’, Esprit 343: 175–88.
Cetina, K.K. and A. Preda (2007) ‘The Temporalization of Financial Markets: From Network to Flow’, Theory, Culture & Society 24(7–8): 116–38.
Chartier, R. (1998) Au bord de la falaise: l’histoire entre certitudes et inquietude. Paris: Albin Michel.
Cohen, F.B. (1984) ‘Computer Viruses: Theory and Experiments’, pp. 240–63 in Proceedings of the 7th DoD/NBS Computer Security Conference. Gaithersburg, MD: National Bureau of Standards.
Connor, S. (1991) ‘Doctor Popp and the Trojan Horse’, The Independent 1 December.
Cooper, M. (2006) ‘Pre-empting Emergence: The Biological Turn in the War on Terror’, Theory, Culture & Society 23(4): 113–35.
Critical Art Ensemble (1996) Electronic Civil Disobedience and Other Unpopular Ideas. Brooklyn, Autonomedia.
Cummings J.N. and R. Kraut (2002) ‘Domesticating Computers and the Internet’, The Information Society 18(3): 221–31.
De Certeau, M. (1975) L’Ecriture de l’histoire, Paris: Gallimard. Detrez, C. (2002) La Construction sociale du corps. Paris: Seuil.
Di Corinto, A. and T. Tozzi (2002) Hacktivism: la liberta` nelle maglie della rete. Rome: Manifestolibri.
Dizzy (1989) ‘Darf Zu Pru ̈ fzweckern von des Post Geo ̈ ffnet Werden . . . ’, picture in Die Datenschleuder 30: 1.
Dyer-Witheford, N. (1994) ‘Autonomist Marxism and the Information Society’, Capital & Class 52: 85–125.
Epstein, S. (1995) ‘The Construction of Lay Expertise: AIDS Activism and the Forging of Credibility in the Reform of Clinical Trials’, Science, Technology, & Human Values 20(4): 408–37.
Epstein, S. (1996) Impure Science: AIDS, Activism, and the Politics of Knowledge. Berkeley: University of California Press.
Fairclough, N. (2003) Analysing Discourse: Textual Analysis for Social Research. London: Routledge.
Featherstone, M. (2007) ‘Ubiquitous Media: Introduction’, Theory, Culture & Society 24(7–8): 319–22.
Fraiberg, A. (1991) ‘Of Aids, Cyborgs, and Other Indiscretions: Resurfacing the Body in the Postmodern’, Postmodern Culture 1(3), URL (consulted September 2009): http://pmc.iath.virginia.edu/text-only/issue.591/fraiberg.591
Friedman, T. (2005) Electric Dreams: Computers in American Culture. New York: NYU Press.
Frohlich, D. and R. Kraut (2003) ‘The Social Context of Home Computing’, pp. 127–62 in R. Harper (ed.) Inside the Smart Home: Ideas, Possibilities and Methods. London: Springer.
Geary, J. (2002) The Body Electric: An Anatomy of the New Bionic Senses. London: Weidenfeld and Nicolson.
Gibson, W. (2007) Spook Country. New York: Putnam.
Gillett, J. (2003) ‘Media Activism and Internet Use by People with HIV/AIDS’, Sociology of Health & Illness 25(6): 608–24.
Grundner, T.W. and R.E. Garrett (1986) ‘Interactive Medical Telecomputing: An Alternative Approach to Community Health Education’, New England Journal of Medicine 314(15): 982–5.
Hamilton, J. (1998) ‘Sun’s Big Burst into Virtual Reality’, Business Week Online 6 February, URL (consulted September 2009): http://www.businessweek.com/bwdaily/dnflash/feb1998/nf80206g.htm
Hansen, M.B.N. (2006) Bodies in Code: Interfaces with New Media. New York: Routledge.
Haraway, D.J. (1985) ‘A Cyborg Manifesto: Science, Technology, and Socialist-feminism in the Late Twentieth Century’, Socialist Review 15(2): 424–57.
Haraway, D. (1989) ‘The Biopolitics of Postmodern Bodies: Determinations of Self in Immune Systems Discourse’, Differences: A Journal of Feminist Cultural Studies 1(1): 3–43.
Harrison, M. (1988) ‘Security Gets Intensive Care: Medical Groups Step Up Protection’, Financial Post 6 June.
Hayles, N.K. (2009) ‘RFID: Human Agency and Meaning in Information-Intensive Environments’, Theory, Culture & Society 26(2–3): 47–72.
Ikegami, C. (1997) ‘HIV Prevention and Community-based Organizations in Japan’, Journal of Acquired Immune Deficiency Syndromes & Human Retrovirology 14(suppl. 2): 51–7.
James, J.S. (1988a) ‘AIDS Computer Conference from Stockholm’, Aids Treatment News 57(20 May).
James, J.S. (1988b) ‘Scientific Justification for Community-based Trials’, Aids Treatment News 65(23 September).
Kalifa, D. (2008) ‘What Is Now Cultural History About?’, pp. 47–56 in R. Gildea and A. Simonin (eds)Writing Contemporary History. London: Hodder Education.
Kocher, B. (1989) ‘A Hygiene Lesson’, Communication of the ACM 32(1): 3–6. Kraut, R., M. Brynin and S. Kiesler (eds) (2006) Computers, Phones, and the Internet: Domesticating Information Technology. New York: Oxford University Press.
Krishnamurthy, S. (2004) Contemporary Research in E-marketing. Hershey: Idea Group Publishing.
Kroker, A. and M. Kroker (eds) (1987) Body Invaders: Panic Sex in America. New York: St Martin’s Press.
Large, P. (1989) ‘Virus Attack on City Computers Foiled’, The Guardian 14 December.
Le Breton, D. (1999) L’Adieu au corps. Paris: Mé́tailié́.
Lé́vy, P. (1994) L’intelligence collective: pour une anthropologie du cyberspace. Paris: La Dé́couverte.
Linzmayer, O.W. (1999) Apple Confidential: The Real Story of Apple Computer Inc. San Francisco, CA: No Starch Press.
Lupton, D. (1994) Moral Threat and Dangerous Desires: AIDS in the News Media. London: Taylor and Francis.
McCloskey, D.N. (1988) ‘Thick and Thin Methodologies in the History of Economic Thought’, pp. 245–58 in N. de Marchi (ed.) The Popperian Legacy in Economics. Cambridge: Cambridge University Press.
Mentor, The (1986) ‘Hacker Manifesto: The Conscience of a Hacker – January 8, 1986’, Phrack 1(7), URL (consulted September 2009): www.phrack.org/issues.html?issue1⁄47
Moravec, H. (1988) Mind Children: The Future of Robot and Human Intelligence. Cambridge, MA: Harvard University Press.
Mungo, P. and B. Glough (1992) Approaching Zero: The Extraordinary Underworld of Hackers, Phreakers, Virus Writers, and Keyboard Criminals. New York: Random House.
Murche, J. (1989) ‘Rogue Disks Hit Computers’, The Advertiser 15 December.
Muri, A. (2003) ‘Of S***t and the Soul: Tropes of Cybernetic Disembodiment in Contemporary Culture’, Body & Society 9(3): 73–92.
Naj, A.K. (1993) ‘Virtual Reality Isn’t a Fantasy for Surgeons’, Wall Street Journal 3 March.
Ory, P. (2004) L’Histoire culturelle. Paris: Presses Universitaires de France.
Painter, A. (2002) Viral Politics: The Power of E-campaigning. London: Politicos.
Pane, P.J. (1990) ‘Man Arrested in AIDS Disk Blackmail Scheme’, InfoWorld 12 February. Peak, S. (1988) ‘Hackers Could Identify IVF Dads’, The Herald 23 June.
Poirrier, P. (ed.) (2008) L’Histoire culturelle: un tournant mondial dans l’historiographie? Dijon: Editions Universitaires de Dijon.
Raymond, E.S. (1998) ‘Homesteading the Noosphere’, First Monday 3(10), URL (consulted September 2009): http://firstmonday.org/htbin/cgiwrap/bin/ojs/index.php/fm/article/view/621/542
Rheingold, H. (1993) The Virtual Community: Homesteading on the Electronic Frontier. New York: HarperCollins.
Richards, L. (1988) ‘The Appearance of Youthful Subculture: A Theoretical Perspective on Deviance’, Clothing and Textiles Research Journal 6(3): 56–64.
Richman, S. (1989) ‘Common Sense Helps in Virus Battle’, Washington Times 20 December.
Rodgers, S. (1985) ‘Medical Files Easy Prey to Hackers’, Courier-Mail 23 July.
Rosenberg, L.B. (1994) ‘Medical Applications of Virtual Reality’, Virtual Reality Systems 1(3): 48–50.
Rosenberg, R. (1988) ‘Wired and Vulnerable’, Boston Globe 6 December. Ross, D.J. (1992) ‘Persons, Programs and Uploading Consciousness’, Extropy 9: 12–16.
Satava, R.M. (1994) ‘Virtual Reality and the New World Order of Medicine’, Virtual Reality Systems 1(3): 6.
Scott, R. (1984) ‘1984: Apple MacIntosh’, TV commercial by CHIAT/DAY.
Singer, L. (1993) Erotic Welfare: Sexual Theory and Politics in the Age of Epidemic. London: Routledge.
Sterling, B. (1986) ‘Introduction to Mirrorshades’, pp. 1–13 in B. Sterling (ed.) Mirrorshades: The Cyberpunk Anthology. New York: Ace Books.
Sterne, J. (2006) ‘The Historiography of Cyberculture’, pp. 17–28 in D. Silver and A. Massanari (eds) Critical Cyberculture Studies. New York NYU Press.
Stone, A.R. (1991) ‘Will the Real Body Please Stand Up? Boundary Stories about Virtual Cultures’, pp. 81–118 in M. Benedikt (ed.) Cyberspace: First Steps. Cambridge, MA: MIT Press.
Stone, A.R. (1996) The War of Desire and Technology at the Close of the Mechanical Age. Cambridge, MA: MIT Press.
Storey, J. (2006) Cultural Theory and Popular Culture: An Introduction. New York: Pearson Prentice Hall.
Tofts, D., A. Jonson and A. Cavallaro (2003) (eds) Prefiguring Cyberculture: An Intellectual History. Cambridge, MA: MIT Press.
Treichler, P.A. (1991) ‘How to Have Theory in an Epidemic: The Evolution of AIDS Treatment Activism’, pp. 57–106 in C. Penley and A. Ross (eds) Technoculture. Minneapolis: University of Minnesota Press.
Turner, B.S. (1987) Medical Power and Social Knowledge. London: SAGE.
Van Loon, J. (2002) Risk and Technological Culture: Towards a Sociology of Virulence. New York: Routledge.
Venn, C., R. Boyne, J. Phillips and R. Bishop (2007) ‘Technics, Media, Teleology: Interview with Bernard Stiegler’, Theory, Culture & Society 24(7–8): 334–41.
Vigarello, G. (1988) Une Histoire culturelle du sport: techniques d’hier et d’aujourd’hui. Paris: Laffont.
Waldby, C. (1996) AIDS and the Body Politic: Biomedicine and Sexual Difference. London: Routledge.
Wilder, C. (1988) ‘Cashing in on Virus Anxieties’, Computerworld 21 November. Wodak, R. (2001) ‘The Discourse-historical Approach’, pp. 63–94 in R. Wodak and M. Meyer (eds) Methods of Critical Discourse Analysis. London: SAGE. Wood, C. (1988) ‘Crime in the Computer Age’, Maclean’s 25 January.
Woods, W. (1989) ‘Computer Guardian: The Sensation of a Shared Virtual Reality’, The Guardian 13 July.
- The domestication of computers, which some commentators date back to the mid 1990s (Cummings and Kraut, 2002; Frohlich and Kraut, 2003; Kraut et al., 2006), was actually a distinctive phenomenon of the previous decade. ↩
- One of the milestones in Apple’s rise to commercial supremacy was a computer christened Lisa, named after Steve Job’s daughter. In the 1980s, another big hitter was Commodore’s Vic20, whose name, according to its creator, ‘sounded like a truck driver’ (Bagnall, 2003). ↩
- Among the best-know nexamples of computer names inspired by childhood are: the IBM PC jr, the Japanese Junior100 and the Danish RC Piccolo. Animal and fruit names were also commercially successful: for example, the Commodore’s Pet was followed by BWV’s Husky and by Applied Technologies’ MicroBee; early European competitors of Apple included Acorn computers and Apricot PC. ↩
- After 1982, a number of short-lived home computers with pretentious names popped up: the Welsh Dragon Data, the English Atom, the Belgian Charlemagne 999, the French Orchidé́e as well as the American Vixen were all forced out of the market by 1984. ↩
- For a complete description see Linzmayer (1999) and Friedman (2005). ↩
- Rushing through the phone line like heroin through an addict’s veins, an electronic pulse is sent out, a refuge from the day-to-day incompetencies is sought [ . . . ↩
- Now established as a landmark publication in hacker history, Die Datenschleuder: Das wissenschaftliche Fachblatt für Datenreisende [The Data Catapult: A scientific journal for Infonauts ↩
- The phrase, created at the end of the 1980s by the art collective Critical Art Ensemble as the title of a joint project with ACT UP was later to be popularized in Critical Art Ensemble (1996). ↩
- The founder of Aids Treatment News, John James, was also the initiator of the seminal Bay Area ‘virtual community’ CommuniTree (Stone, 1991). The director of Critical Path, Kiyoshi Kuromiya, was a top name in the electronic activist milieu of Philadelphia. ↩